|
Here is a list of tips. You can scroll down to read about each one, starting with operating systems:
- Operating Systems - Everything You Didn't Want To Know About Windows!
- Virus and Trojan Horse Threats
- How To Stop A Hacker
- Backing Up Your Data and Organizing Your Hard Drive
- Programs loading more slowly than they used to?
- Does Your Monitor Seem To Flicker and Give You Headaches?
Operating Systems:
The Windows 2000 home page, viewed on a Windows 2000 computer
Example: Windows Millenium (Me) and Windows 2000, two operating systems with almost the same name, are VERY different products! With so many Windows operating systems, some of us get confused as to the differences. And... we all know that Mr. Bill Gates' operating systems do not come cheap! So it's important to understand a little about the history of these systems and how they are different.
Because most of us probably have Windows 95 or newer, I will go back to 1995 and start there. Basically, Microsoft's operating systems took two very different tracks in 1995: One was the product meant for home use, and the other was meant for business use in larger corporate settings. Now on the home front we had Windows 95, an outgrowth of Windows 3.1. Really when it comes down to it, Microsoft was trying to copy the Graphical User Interface (the desktop with pictures and icons to click on instead of just a black screen with white letters that have to be exactly right to work) of Apple Computer's MAC product. Early versions of Microsoft's DOS had what is known as a "command line" interface (the black screen with the exact syntax required to execute programs), which was pretty much meant for the exclusive use of companies like Big Blue (IBM), you know, computer geeks! But Microsoft knew that if it was to get with the program and bring a useful product to the everyday home (and business) user, it needed to get that Graphical User Interface from MAC (and also the mouse, originally created by Xerox). Bill Gates was once quoted as saying "Good men create, great men COPY!". Thing of it was, Bill did not keep his operating systems exclusive to IBM only, he licensed them to anyone wanting to build computer systems, and this is why Windows 95 took off like a grass fire, because it was on virtually every system built.
All home products - Windows 95 (four versions were produced), Windows 98 and 98SE (Second Edition), and Windows Millenium - all these products up to Me - were based on DOS. The operating system sat on top of DOS, and all the graphics and pictures were merely pathways that still led to the command line of DOS code to execute.
Memory: Now a long time ago, Bill Gates was once quoted as saying that no one will ever use applications that need more than 1MB of RAM! Just look at any of today's computers to see how wrong he was! But my basic point here is that ALL these systems based on DOS, even the so-called modern Me, were confined to this 1MB limitation, with 640 kilobytes being assigned to what is known as conventional memory. These systems constantly fight over how to assign memory to today's 32-bit applications. I'm sure all of us have experienced the "Blue Screen of Death", the freeze-up that occurs with these systems, one of them occuring before the whole world during an operating system roll-out, and the presenter, standing alongside Bill Gates, was promptly fired!
Another aspect of the old DOS systems was that applications and the operating system kernel were given direct access to hardware devices, another reason for the all-too-often lockups we all experience. This is not to say that the products were not improving. Windows 95 was signifigant in that it was a bridge between the old 16-bit DOS world and the new 32-bit applications that were being developed. Another key feature of these systems was the idea of "Plug and Play", that home users could install hardware devices and the operating system would have the appropriate hardware drivers to allow them to be installed more or less automatically, making it much more convenient for the home user.
OK, now that (whew!!!) we have looked at the home market product, let's examine the products that were developed along the business side, and then we will see how it all comes together for today's XP:
in 1994, Microsoft rolled out their product for network servers and workstations (the name given to the corporate equivalent of the home desktop machine). This product was called Windows NT 3.1. This is the blood line that today's Windows 2000 and XP comes from, married with the best features of the home product. NT stands for "New Technology". Microsoft decided to make a clean break from DOS with this product. When Windows NT 5.0 was released, it integrated the Internet Explorer Internet browser along with the operating system, perhaps the key sticking point that led to the U.S. government's cracking down on the company, as this pushed the competition into the background, and gave Microsoft what was considered to be an unfair advantage. But, I digress...
Another key feature of the NT product was a new file system, called NTFS, or New Technology File System. This was a much more organized way of storing data on hard disks, allowing for extra security such as encryption and compression of data, and allowing for much larger volumes for storage.
Now - back to memory: Both Windows NT and it's successor, Windows 2000, use something called paging files to organize memory. Gone altogether are the old limitations of DOS. Windows 2000, one of the very best if not THE very best operating system ever made, uses memory wherever and whenever it needs it. Windows 2000 was also beefed up with with an impressive lineup of hardware drivers, making it more "Plug and Play" like the home products. Unlike the home product Me, which was rushed to market to make a chronological deadline (the year 2000), Windows 2000 had a long and extensive and well-tested development period. It was and is a very well thought out product. Ask any technician, at IT educational institutions, or out in the field where they deal with customer problems everyday, and they will tell you, this is a good product. Most of us technicians actually prefer it to XP, because the tools that give it power are not hidden the way there are on XP.
Windows 2000, and now XP, is a fully modular system. That is to say that the core (called the kernel) of the operating system is protected and isolated from ill-behaved applications and from hardware. Bottom line, if something messes up, it doesn't bring the whole system down like the Windows 9x systems did. Old 16-bit code applications run in virtual windows, thinking that they are still in an old DOS computer but they are not, and if they mess up, well, they get kicked out! Any process can be isolated and shut down by the user (even critical ones the system needs to run, so be careful!).
So...what is XP? XP comes from the NT/Windows 2000 bloodline. It uses NTFS (although you can still use the older file system (called FAT 32) that Windows 9x used if you want to run both operating systems on the same computer (best done on seperate partitions, as a dual boot, but not for the faint of heart! I've lost some good data experimenting a little too much with such things, but how are ya gonna learn, right?). It gives full control (although in my opinion Windows 2000 did this even better) over users and groups, granting rights and privileges accordingly. Now I am talking the Professional, not Home version here, just to give you the big picture. Also, objects like files and folders can have permissions granted to them, as to who can access them. Another feature is that audits can be set up that tell when problems occur and keep logs of these problems (many of them are kept automatically), or issue alerts or even execute certain programs automatically when specific problems occur. Many places, like public libraries, use Windows 2000 (and now XP) and completely lock it down so that only a very limited functionality is available to the end user (although it's tempting for Windows 2000-savvy techs to try to mess with them!).
XP, like Windows 2000 before it, incorporates a large set of built-in drivers, making it "Plug and Play", and easy to install hardware devices on. Do be aware of one thing, though: XP, like Windows 2000, has something called an HCL, or Hardware Compatibility List (viewable at microsoft's website). Any devices you put on either of these operating systems MUST be on this list. Especially with XP, which requires that drivers must be "digitally signed" (in so many words, approved for XP), this must be observed. XP will simply reject some drivers that are not, or can be made to load them, but they sometimes will not work. I found this out with a particular brand of Network Interface card that supposedly was XP compatible. It kept dropping the connection to the Internet, but a different model with a driver on the XP list fixed the problem. So, if you are upgrading from older systems, be prepared for a bit a driver issue if your hardware is not on this list (most are, however).
And for the home user? XP is great for applications like multimedia, photographs, music, video. For watching live shows broadcast over the Internet. And of course it has that great bloodline that is at the very minimum all 32-bit code, no memory problems (supports a huge amount of RAM), and interfaces very well with today's high speed hard drives and processors. XP can be added as an upgrade to versions of either the Windows 9x line (98SE on up, including Me), or the Windows NT/2000 line. For those who are used to the older Windows 98 and Me, XP will probably take a little getting used to (the appearance of it is decidedly changed), although you can switch to classic mode view if you wish.
So...Remember our little example at the start? Windows 2000 IS very different from Millenium, isn't it? And now you know... probably much more than you ever wanted to... why!
Virus and Trojan Horse Threats:
Norton Anti-Virus and Norton Personal Firewall
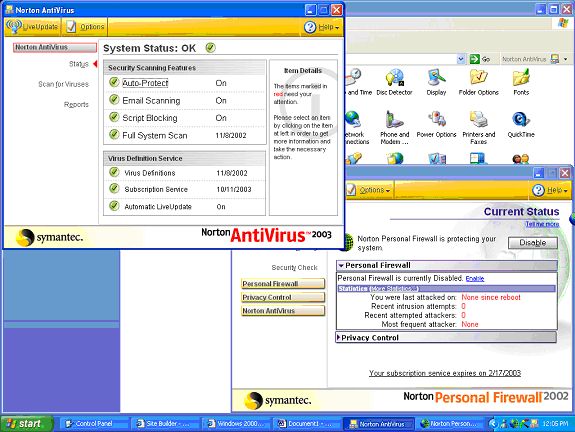 I cannot stress enough the importance of two main types of protection that you absolutely must have on your computer, especially if you go online.
The first is virus protection. And by this I don't mean whatever came with your computer and then forget about it, you are protected. You are not protected! You must, as part of your virus program, have an ongoing subscription, sometimes called "Live Updates" or other such name. These need to be updated at least once a week.
You might be surprised how often new viruses are introduced into the world. Computers are tools, very useful tools. There are those out there who think it's funny or perhaps it gives them a sense of control to take away that usefulness from you. The computers we use are based on technology, and some choose to find clever ways to defeat it.
Fortunately, there are diligent companies out there that offer a good and useful service to all of us that rely on the computer as a tool. Two major companies I recommend are Norton and McAfee. Personally, I use Norton (the actual company is called Symantec) for their Anti-Virus product, but this is a personal preference. The subscription service is free for the first year, and only $3.95 per year after that, and well worth the cost. What you are mainly subscribing to is a virus definition service. Whenever a new virus is introduced, these companies define what the virus is, and when downloaded to your computer on a regular basis, they alert your computer when you have received malicious code. In other words, they give your computer the ability to know what to look for. In the case of email that may contain a virus, the program can instantly alert you. The incoming email message and any attachments it may have are immediately scanned. You usually have a choice as to whether to:
- Delete the infected files
- Attempt to fix them
- Quarantine them where they can do no further harm until you decide what to do with them.
Also, you should run a complete scan of your computer's storage drives at least once a week, with a fully armed anti-virus program that is up to date on it's virus definitions. This will scan all the files on your computer, even those that are loaded into memory and that can be then re-written to one of your drives. If you don't have the money to buy the product right away, you can sometimes go to the website of an anti-virus provider and they will scan your hard drive right from their website for free. I found a kakworm virus on my computer this way, and was able to keep it from doing any further damage until I could afford to buy their program.
If you do not practice this method of protecting your computer, you may allow malicious code to enter your computer and not even know it. These viruses, some of which are called "worms" can then spread throughout your computer and attach themselves to your outgoing email messages, possibly infecting everyone on your contact list as well.
You may experience what appears to be computer hardware and software problems, but in actuality there can be an infection running rampant in the background, and it is usually not too long before it becomes foreground, as the virus matures to it's "payoff", which can be some sort of total system shutdown accompanied by a clever little message, and the resultant total loss of your data!
Trojan Horse programs: When you go online, you are using something called a port. Your email uses one such port, and your Internet browsing is done using another. A port in this sense is not an actual hardware connection, but what is known as a logical one, created by software. Computers expect to be able to communicate out into the world using certain "known ports". There are thousands of possible ports that can be used, more than just the few commonly used ones.
What happens is that there are those out there that use automated ways of scanning all the possible ports, looking for chinks in the armor, so to speak. Most computers, with the default settings, have plenty of chinks in the armor! When a usable port is found, a Trojan Horse program can be transferred and placed on your computer. This can happen and not be detected by your anti-virus program. Once on your computer, this program can launch and set up conditions that will allow a hacker to come back and gain access to your computer. It is possible for them to see everything on your computer!
How do you protect yourself from this? You install what is known as a "firewall". This can be a device, but a firewall is software, whether it's part of a device or just loaded as a program on your computer, that controls and limits access from the outside world to your computer. It shuts off all access to these ports, making your computer invisible to the outside world. On a stand alone home-use computer, this may be called a "personal firewall". In corporate settings, it may be a more sophisticated setup, that stands between the outside world and the company's interior network of computers.
On a home machine, this program can be set for:
- How much information you choose to receive from it, warning you of important things like attacks that have occured, or of things called "cookies" that are placed on your computer by Internet sites out there, so that they can better communicate with your computer on subsequent visits. The amount of this kind of activity can be controlled by you.
- How much access you want all of your programs to have to the Internet (your computer communicates with the world more than you might know!). You can limit the access your programs have to the Internet, and which ones are allowed to have this access.
- Security Checks: You can have the program go to it's parent site and have the company that provides this service attempt to gain access to your computer. They will scan your computer's ports and report back to you how safe you are from intrusion.
Again, this is a matter of preference, but I use Norton's Personal Firewall product for this purpose. The firewall and anti-virus products work in concert together, and when you get the latest virus definitions, you also get the latest Trojan Horse definitions as well as improvements to either program, on the same download list.
You can either go to the company's site for these regular updates, or set up your computer so that you automatically receive the updates whenever you are online, similar to receiving regular updates to the Microsoft operating systems.
One note on firewalls: Because you are invisible to the outside world, some features will not work when your firewall is enabled. If you use Instant Messenger for webcam and voice conversations, you may have to temporarily disable your firewall. If you use NetMeeting, however, and if the party you are trying to call is not behind a firewall, you can still be protected behind your firewall and still carry on a video and voice conversation.
Also, if you have a home network set up, and you use TCP/IP for your home networking protocol, you will not be able to see each other's computers if each computer has a personal firewall enabled. What you can do is use one of your computers as a shared Internet connection, using two network interface cards: One for the home network, and one for the Internet connection. Make the Internet connection a firewall protected connection. Then disable the personal firewalls of each computer on the home network, and use a second network interface card on your main computer for it's participation in the home network. All the computers will be connnected to the hub or switch, but the Internet is not (see illustration of this setup on the services page near the bottom). This protects your home network computers from exposure to the Internet, even though they can still go out to the Internet via the shared connection of the main computer using the seperate network interface card (or NIC). Since that connection is protected by a firewall, the home computers are safe from intrusion, but they can still see each other within the home network by virtue of their own NICs being connected to the central hub, with the main computer also having it's own seperate NIC for that purpose. This scheme allows you to safely use the standard TCP/IP protocol that is used on the Internet, without exposing you to the risks.
There are also some ways of accomplishing this without so much hardware complexity by using protocols for your home network that are not used out on the Internet. Oh well, if it all get's to be a little too bewildering, just call Glen's Computer! He'll have to do all the worrying! (Not that everyone wants to go overboard like Glen does when he is fooling around with his home network!)
How To Stop A Hacker
Most people let the computer assume that the person starting the computer is the primary user, and that person is not asked to log on to the system. In most cases, this gives the user full administrative power to not only read all files, but also to change them, including critical system files. Now if a hacker gets access to that computer while the user is online, that enables them with full power! So it might be a good idea to consider creating seperate user and administrative accounts, and only going online when you are logged in as a limited user.
The user accounts would have only limited access to files: read-only, not allowed to write and save changes. The administrative account would enable you with full power, when you needed to load new programs, and make other important changes. Use a password on this account that is difficult to guess. For example, do not use a word that can be found in a dictionary. Some hackers will launch what is know as a dictionary assault, going through every possible word until they have a hit. Mix upper and lower case letters in your password. Mix in numbers with the letters. For example: MypaSsw0rd, where in this example, I used the number zero, not the letter O, and mixed in a couple of upper case letters.
If you have Windows 2000 or XP Professional, another good idea is to create the necessity of having to hit the Ctrl+Alt+Del keys to even have the privilege of logging in. What this does is create a situation where the computer is looking for input from a local hardware device: your keyboard. This can not be faked over the Internet! Only someone physically sitting at the computer can access it.
Another feature of Windows 2000 and XP Pro is the ability to lock out the computer after so many failures to enter the correct password. This is another measure that defeats organized attempts to guess at the password, such as dictionary assaults. These systems also allow a person to audit failed attempts to log in to the computer, and even set the audit so that an alert is issued after so many failed attempts.
Backing Up Your Data and Organizing Your Hard Drive
Checking off files to back up
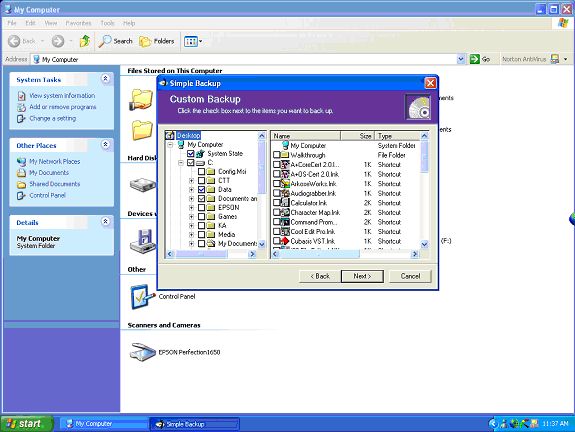
I'm going to deal with two subjects at once here, as they are both intertwined:
- How we organize the data on our hard drives
- How we back up that data
Data on our computers tends to get scattered and sometimes it gets lost. We don't mean for it to happen that way, it just does. One thing that happens is we allow programs to install files in default locations that the application chooses. After the programs are installed, when we click "Save", our work that we have done is most often stored in default locations created by those same programs. Sometimes we don't pay attention to where something was saved and we forget where it went. And if we go searching for all those locations, it can be hard to find them all. Keeping a computer organized sometimes takes a conscious effort on our part. We need to take take control of the process.
Now the reason I bring this up is not only that I am going to make a couple of suggestions on how to organize our data, but also how to back up that data in case we should lose it due to some system or device failure. And if we organize it correctly, it will be that much easier to back up.
Someone once said that data doesn't exist unless it exists in more than one place. I think this is a healthy way to think about it. Some of the work we do on our computers may have taken only hours to create, but we all know that some of our work represents years of effort. We tend to take for granted that this work will be there everyday when we go to access it. But what if we went to get at our work one day and it was all gone? It never happens when you expect it. One day you go to find the data you take for granted to be there, and it has already dissappeared forever, and there is nothing you can do about it. And it hits you... My God, all that work, all those precious photos, etc., all gone, and we wish we had done something to prepare for this.
What we need to do is back up our data. It may seem like a tedious task, taking us away from our daily work, but it is so important that we develop this habit. Some operating systems have their own built-in utilities for doing this, and by all means use any tool at your disposal, but I am going to suggest a third-party product. It is called "Simple Backup", produced by a company called Veritas, who make such programs for big corporations. Lucky for us, they made a simple, easy-to-use product for us home users as well. It only costs $29.00, and can be downloaded from Stomp.com.
What you do is check off all the folders and files you want to back up, and then the program creates one big file out of all of them, compresses that file, and spans it over as many CD-Rs or CD-RWs (CD-Rs are written to once, CD-RWs can be written to again and again) as is necessary. If you suffer a total system failure and lose all your data, you simple load these CDs one at a time and like magic, all of your folders are restored to their original places. I came so close to disaster when a hacker took my XP system down, and I had only done one backup. When I loaded the disks, it was like a miracle seeing all my photographs and letters and so on, all coming back. Even the Simple Backup program itself, which was also lost, was now coming back. You do not need the program installed to restore your files!
Now this brings us back to organizing your hard drives. What you can do is anticipate the backup process in the way that you do this. What I suggest to do, is to create two folders: One called "Data", and one called "Utilities". Rather than merely hitting "Save" after working on a project, I suggest selecting "Save as" instead, and rather than allowing a program to save the work you do to it's own default folder, browse instead to the Data folder, and save the file there, in a subfolder that has some sort of logical name that you will remember. Do this with ALL of your files that you spent any serious time on, or anything (such as photos) that you would not want to lose.
Also, every time you get a utility that is not located somewhere on a CD, like those you may have downloaded from the Internet, place that program (or driver or any other software you have that is not on a disk) in your Utilities folder. These can be difficult to chase down later and find them all again if they were lost.
Now, when you go to back up, you can check the boxes for these two folders, and know, in this one simple step, that all of your work will be safely backed up!
Another thing to consider when organizing your hard drives is that you do not want too many miscellaneous files located at the root of your drive, usually drive C. This is where your system files are located. So if a program that you are installing wants to install to a folder at the root of your drive (for example, the program asks: "install to C:\<name of program>?"), you say no, I want to redirect it to a folder called "Program Files" (C:\Program Files\<name of program>), and then let it create it's folder there. These usually do not have to be backed up, by the way, because you have the original CD the program came on. Now sometimes programs insist on installing at the root, and won't run anywhere else, but only occasionally does this happen. Try at least to keep those loose files like individual text files and so on from living at the root of your system drive.
One final note on backing up: You can have the option to back up the system or configuration files, sometimes called the System State, the files that are located in the Registry of your computer. Backing these up will restore many of the settings of your computer, and it will restore your computer to all that is familiar to you in the case that you lose everything.
Now I am going to describe an alternative method of backing up: Ghosting. Ghosting involves a program created by Symantec, called Norton Ghost. What this involves is sort of like taking a picture of your entire hard drive, capturing an "image" of the entire drive. That mirror image of your drive is then transferred to another drive. Ideally, the second drive should be the same size as the first and formatted the same way, as the image is expecting to land on a drive that has the same structure, or "low level formatting" as the original. This drive now contains all that is necessary to boot your computer with as if it were the original drive, as well as all of your data.
A side note: Newer motherboards now support something called "RAID", or redundant array, in other words multiple drives that can be either be written to simultaneously (called "striping"), or can automatically create a duplicate image (called "mirroring") of the first drive. The first option is for performance or speed, and the second is for backup, and hence slower, but more secure.
And one poor man's way to back up: Simply copy some important files to a floppy or other removable storage media. Anything to protect your work!
So in closing, always pay attention to where things are being stored on your computer. Write them down if necessary. If you lose track of them, but you can remember the filename, you can locate them using your "Find" or "Search" utility. Be selective about where programs ask to place files, and don't be afraid to step in and create useful major folders like the Data and Utilities ones I have suggested as examples. These can easily be selected for backup, and you will have the peace of mind knowing that all of your important work will be protected in the event of a disaster.
Programs loading more slowly than they used to?
The Disk Deframenter tool
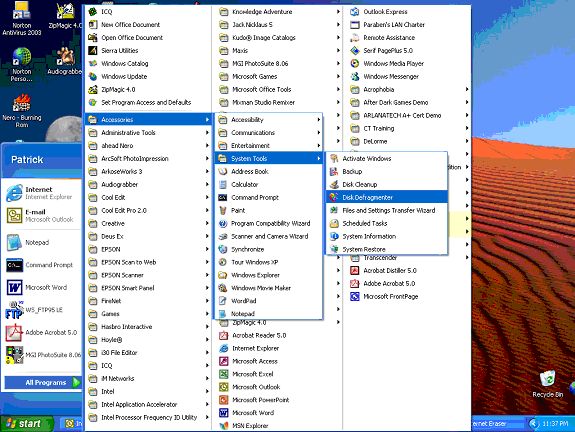 An item of maintenance that we often overlook is the Disk Defragmenter tool, which can signifigantly improve the performance of our computers.
Explanation: Everytime we save files on our computers, we write them to the next available space on our drives. Trouble is, that spot is usually a long ways off from the same file, the last time we made changes to it, using the same application. So what happens is that our files become "fragmented", a little piece here, a little piece there, scattered all over the drive. And when we ask the computer to load a program or to find a file that it used to find as just one piece, it is now looking for many pieces, which explains why it takes so much longer than it used to to load all of them into memory.
What we can do is use the Disk Defragmenter tool. This program finds all those little pieces of files (called noncontiguous files), loads them into memory, and rearranges them onto your hard drive again as one whole, continuous file again. Now when we ask the computer to find that file, it is all in one place again, in one piece. Our entire drive is now a collection of whole files and programs again, and we once again pick up that performance we used to enjoy.
On most Windows computers: Use the Start button, go up to Programs, select Accessories, select System Tools, then select Disk Defragmenter.
Does Your Monitor Seem To Flicker and Give You Headaches?
Sometimes when we get our new computers we jump in and start to use them and never get around to setting something called the "refresh rate" of the video driver for our monitors. Or, we may install the latest version of Windows and use the default settings for the monitor after it is installed, and we may suffer away for the longest time looking at a screen that flickers too much and gives us headaches. I personally have diabetes, and a flickering screen really bothers my eyes. One of the first things I do when I install an operating system on one of my computers is adjust the refresh rate so that I can stand to look at the monitor while I continue to install drivers and otherwise finish working on the machine.
What is the refresh rate? The electron beam that is deflected across our screen to paint our desktop, line by line (some monitors paint every line, some every other line), is controlled by something called the horizontal oscillator, with a vertical "flyback" when it starts over. An entire painting of the screen is called a "frame". How many times that frame is painted in one second is the refresh rate. Many of the drivers we install for our video cards are left at the default settings, and this beam paints our screen too few times for comfortable viewing.
Now I am going to show you how to look at what your setting is and how to change it. But...I do so with a caution: Not all monitors can support every possible refresh rate, and setting a refresh rate that the monitor is not rated for can damage or even destoy it. Having said that, I will give a couple of tips that should help you get better viewing without too much risk.
To view the refresh rate: Right click on a blank part of your desktop screen. Select "Properties". Click on the "Settings" tab. Click on the "Advanced" button. Click on the "Monitor" tab. OK, here is where you view the refresh rate for your monitor. Often, this rate is set to 60 Hz, which is the minimum setting, and if it is set to this rate, you likely have a screen that flickers quite noticably. Now, here is a safe thing to try that will not damage your monitor: Pick a setting from the drop-down list called "Optimal". This will automatically set the rate to a better, yet safe setting. Now, most modern monitors will support safely up to 80 Hz refresh rate. I am not making a guarantee here, but I have not run into one yet that wouldn't support at least 80 Hz (and we had some fairly crappy monitors at school). Often, the rates that the monitor will support will be automatically displayed. In other words, if the monitor supports 80 Hz, 80 Hz will be on the list. If it would rather support 85 Hz, then THAT will be on the list. In any event, choose a setting that is on the list, most safely the "Optimal" one.
Moving from a 60 Hz to 80 Hz refresh rate will give a much more easy-on-the-eyes display, and 80 Hz is usually not the highest rate it will support.
|